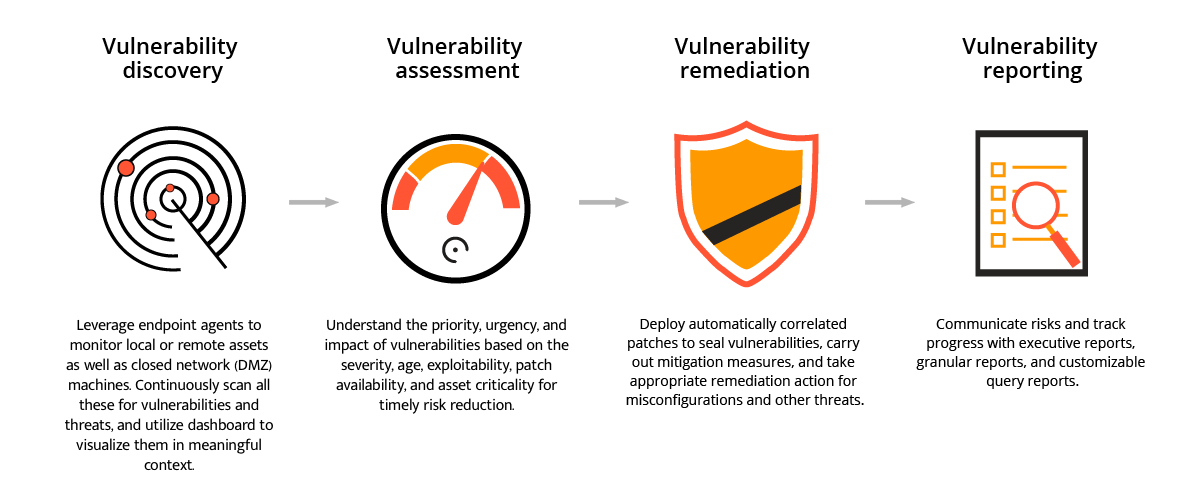
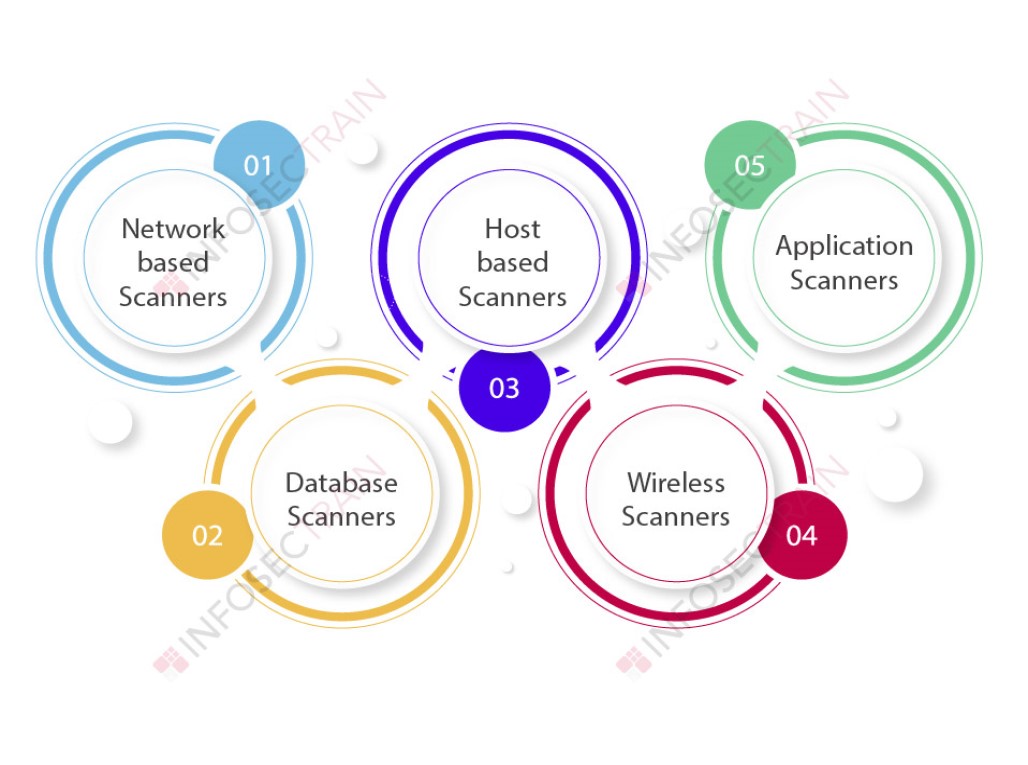
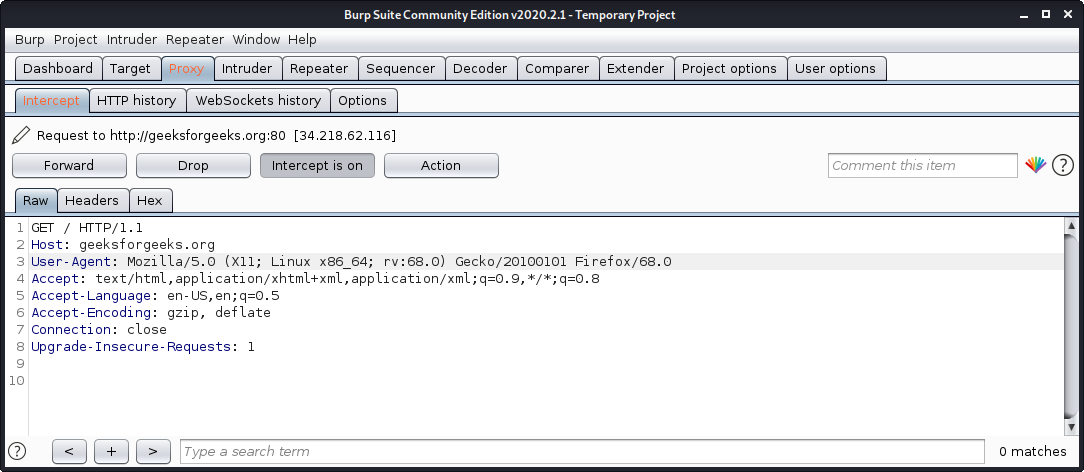
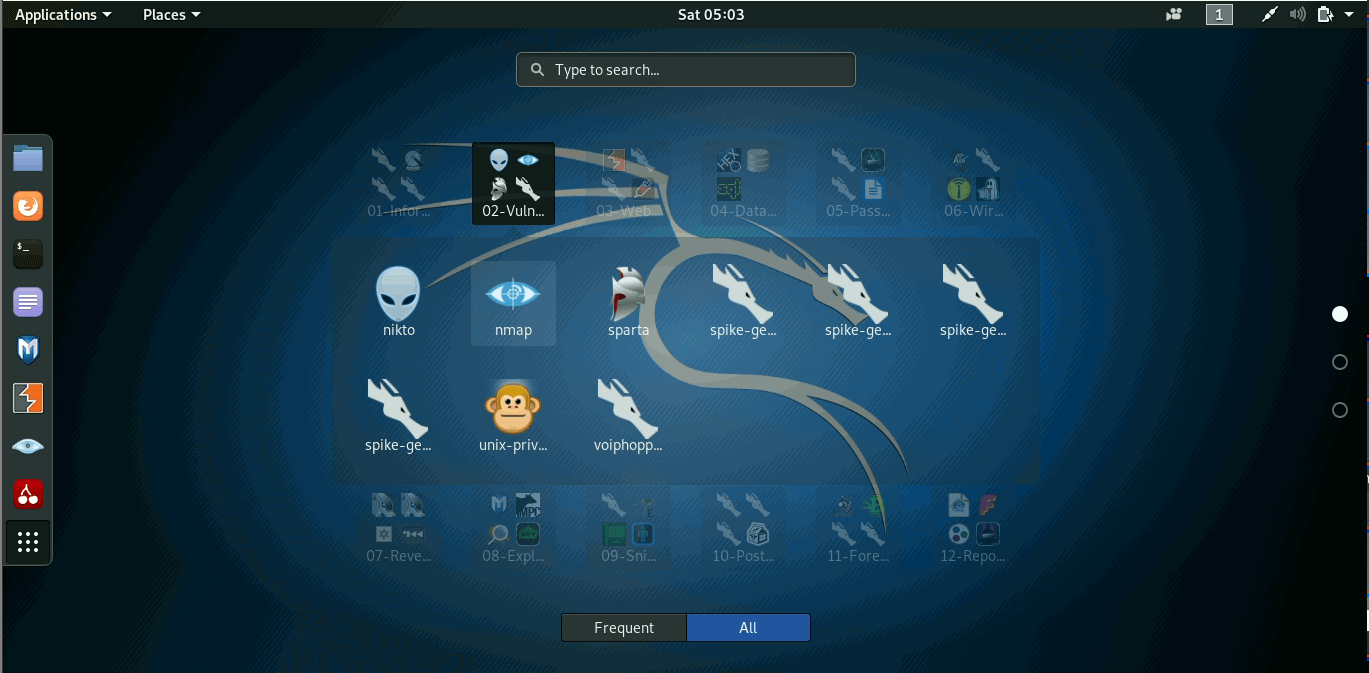
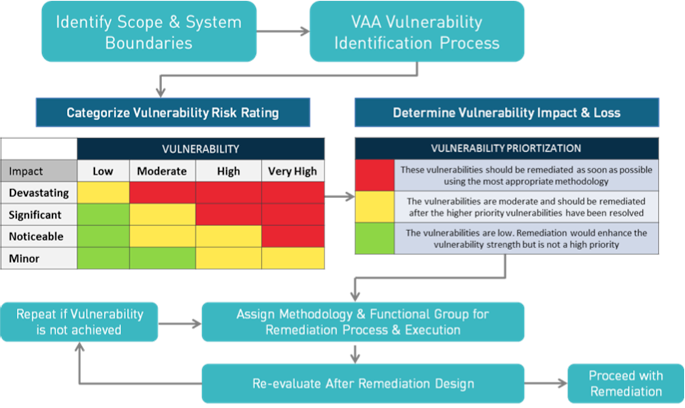
2. Vulnerability Analysis | Analysis and Mapping of Impacts under Climate Change for Adaptation and Food Security (AMICAF) | Продовольственная и сельскохозяйственная организация Объединенных Наций
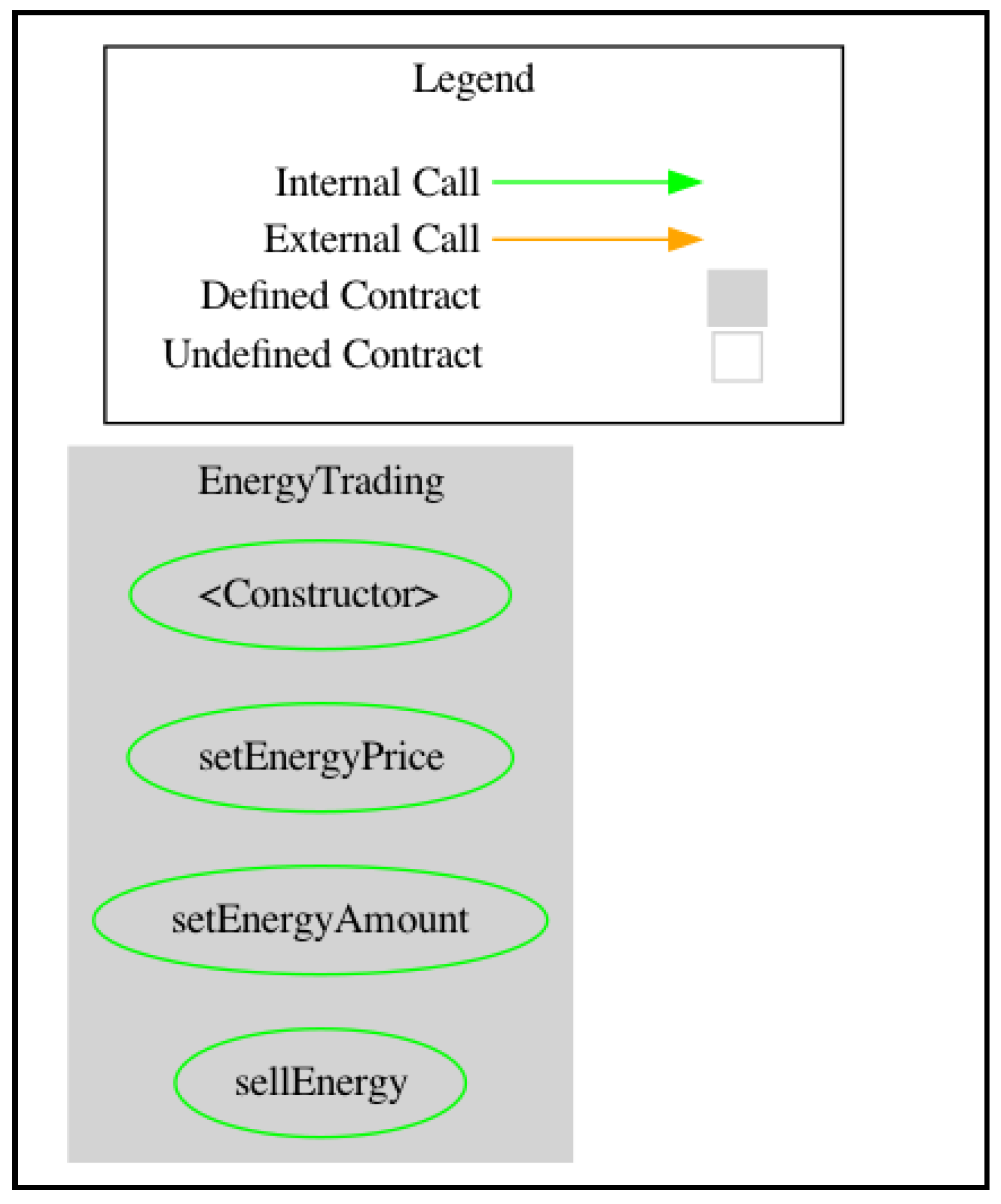
Information | Free Full-Text | Evaluation of Smart Contract Vulnerability Analysis Tools: A Domain-Specific Perspective