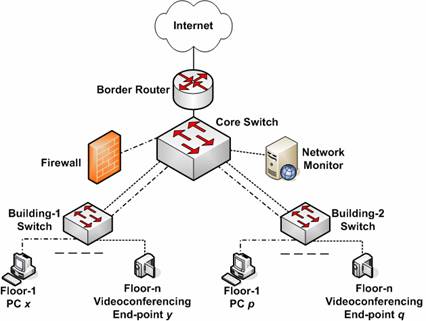
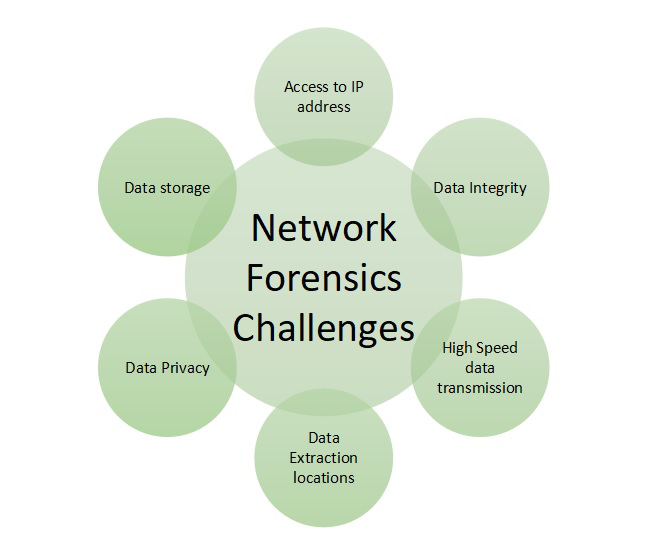
![PDF] Comparative Analysis of Network Forensic Tools and Network Forensics Processes | Semantic Scholar PDF] Comparative Analysis of Network Forensic Tools and Network Forensics Processes | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5a915ae78daa59946bb0888a2ad7a1e168daa360/2-Figure3-1.png)
PDF] Comparative Analysis of Network Forensic Tools and Network Forensics Processes | Semantic Scholar

Generic Framework for Network Forensics ? Preparation Stage : The main... | Download Scientific Diagram
GitHub - mesquidar/ForensicsTools: A list of free and open forensics analysis tools and other resources




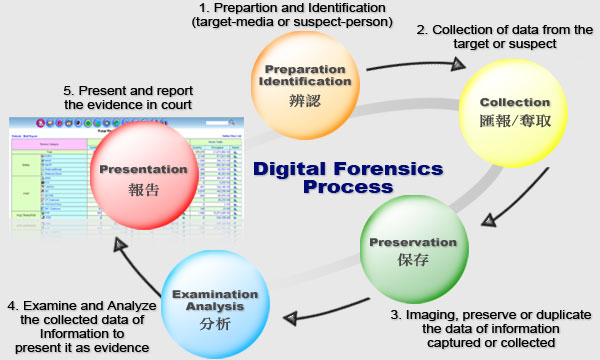
![PDF] Network forensic frameworks: Survey and research challenges | Semantic Scholar PDF] Network forensic frameworks: Survey and research challenges | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/85947d646623ef7ed96dfa8b0eb705d53ccb4efe/7-Figure2-1.png)