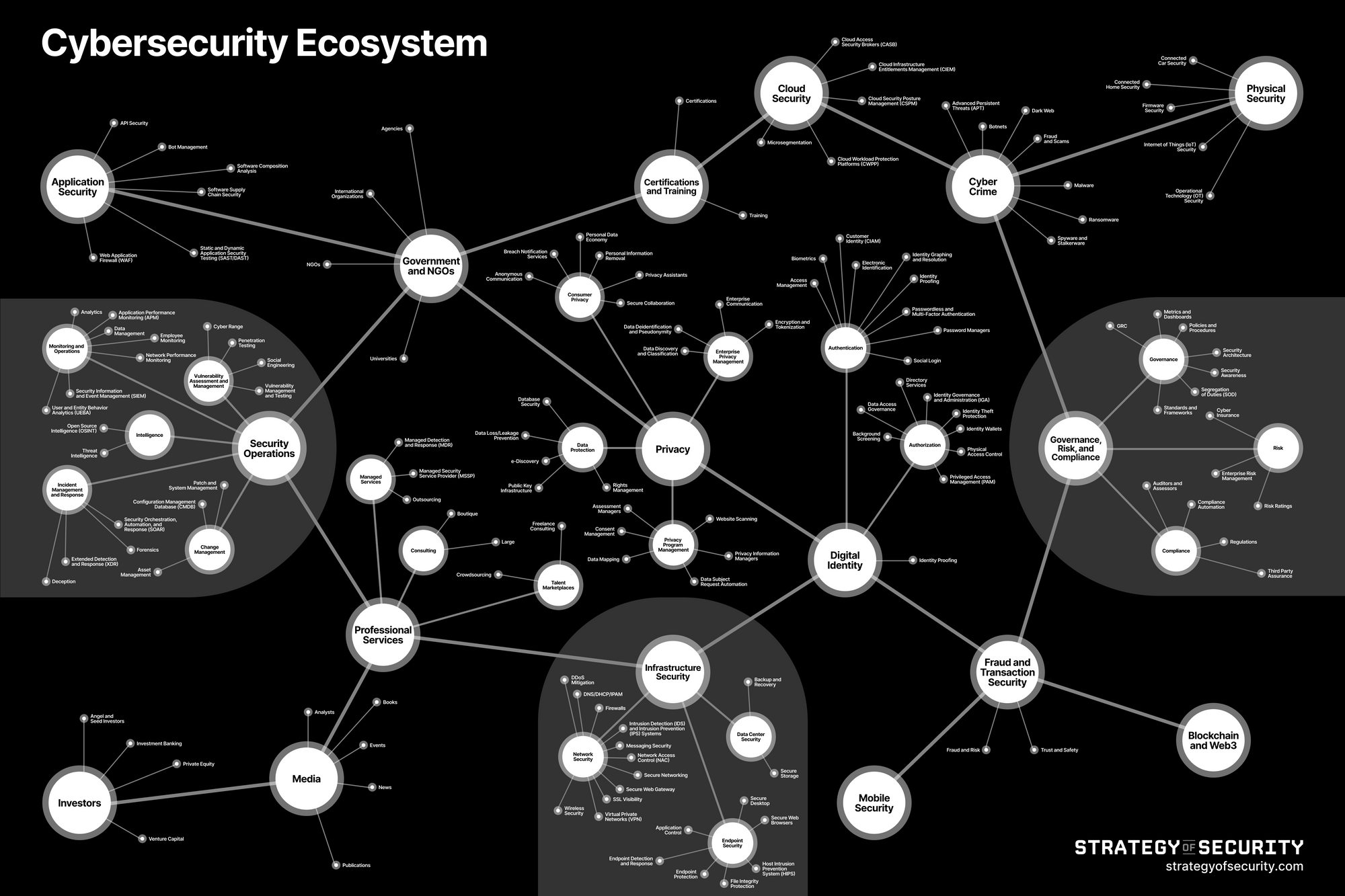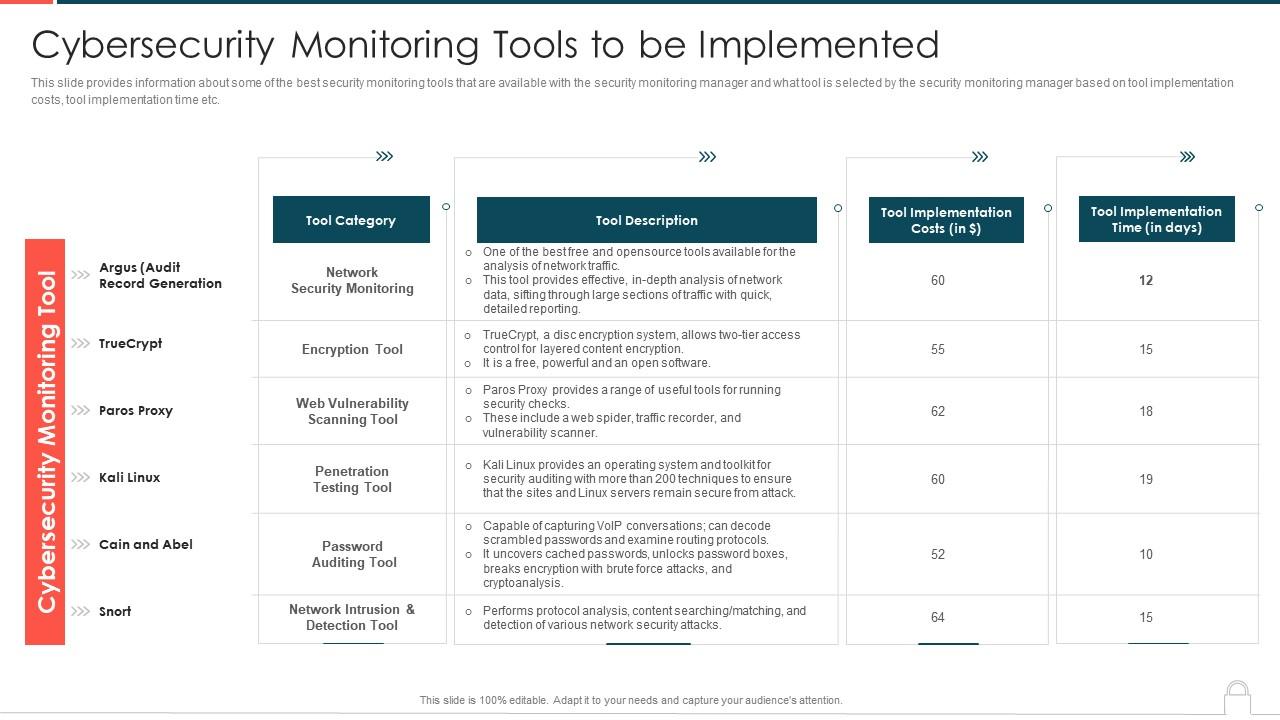
Ways To Set Up An Advanced Cybersecurity Monitoring Plan Cybersecurity Monitoring Tools To Be Implemented | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

4 Steps to Ensuring Efficient Cybersecurity Monitoring in US Educational Institutions | Ekran System
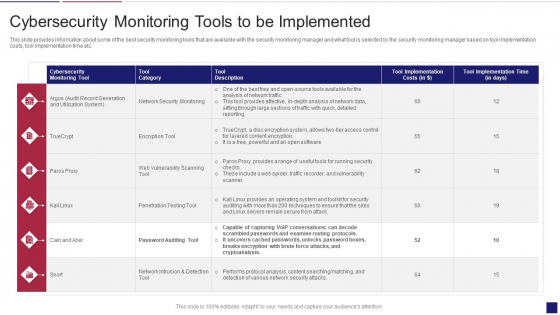
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Tools Diagrams PDF - PowerPoint Templates




![Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES] Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES]](https://www.cimcor.com/hubfs/Cybersecurity%20Lifecycle.jpg)
![Top 20+ Cyber Security Tools for 2023 [Paid+Free] Top 20+ Cyber Security Tools for 2023 [Paid+Free]](https://intellipaat.com/blog/wp-content/uploads/2021/06/Top-20-Cyber-Security-Tools-Big.png)