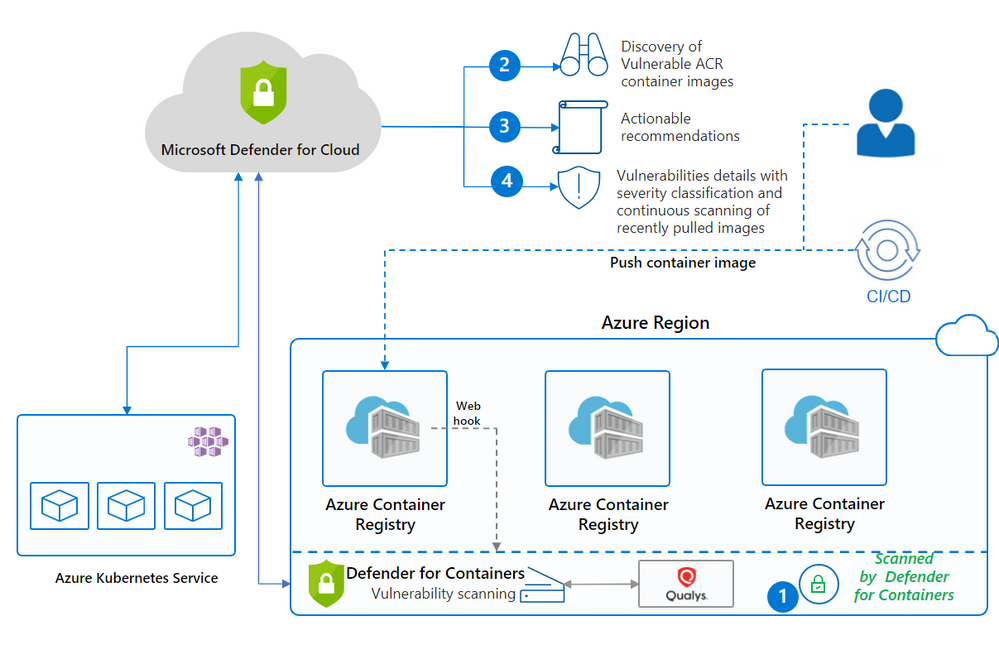
Enhance your CI/CD deployment by using Vulnerability Assessments from Microsoft Defender for ACR - Microsoft Community Hub
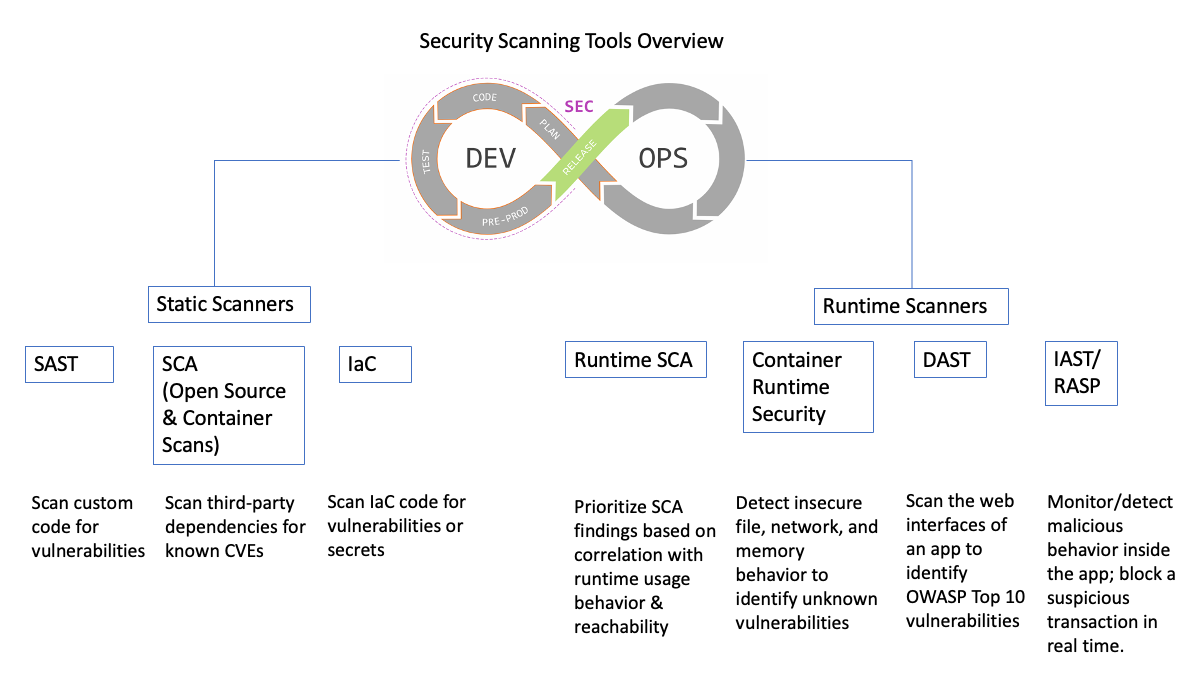
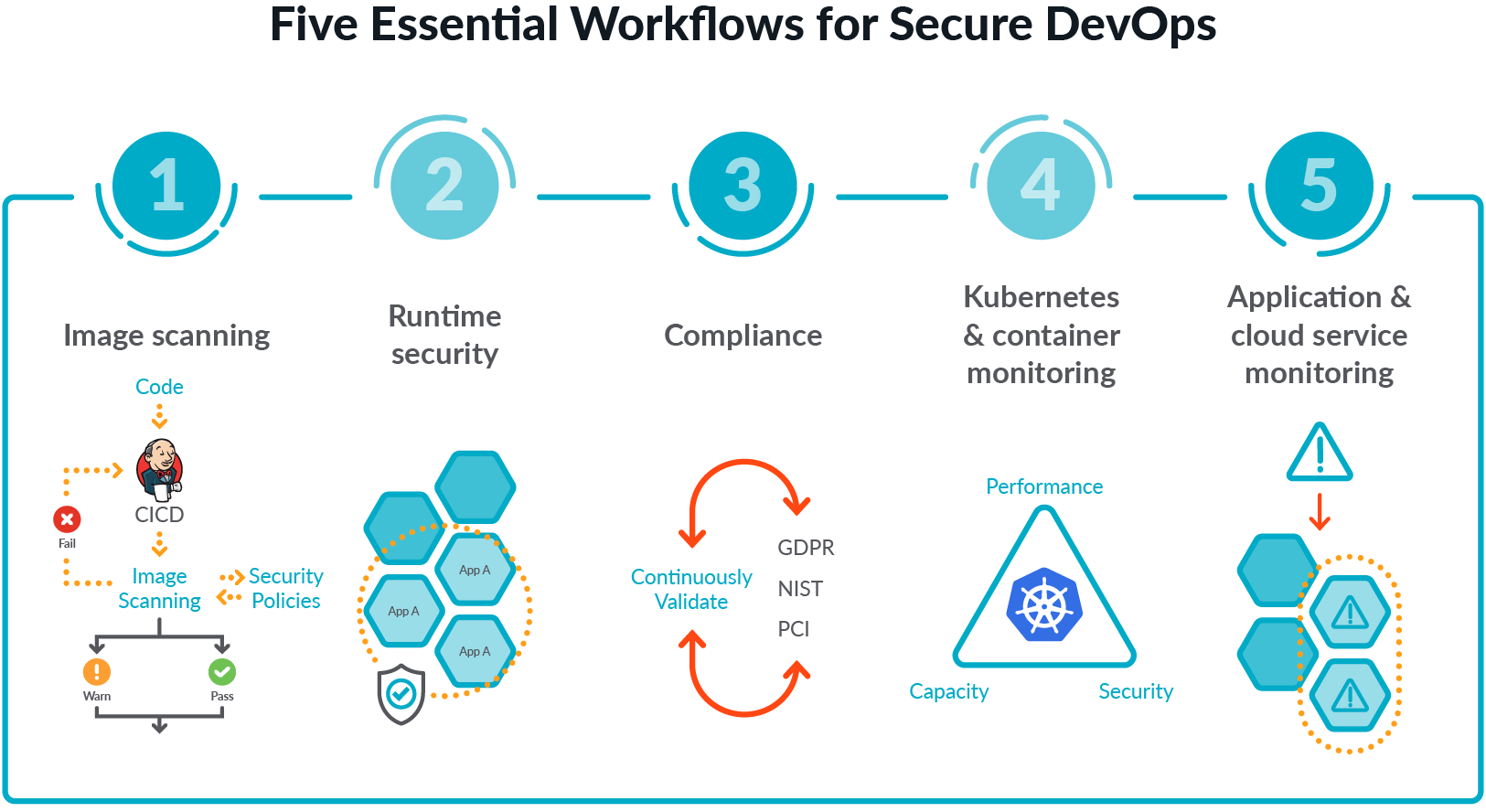
Security Scanning Tools Defined: SAST, IaC, SCA, DAST, IAST/RASP, Container Runtime Security and Runtime SCA - Deepfactor
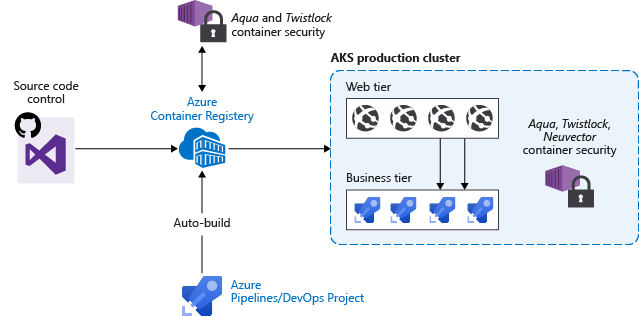
Operator best practices - Container image management in Azure Kubernetes Services (AKS) - Azure Kubernetes Service | Microsoft Learn

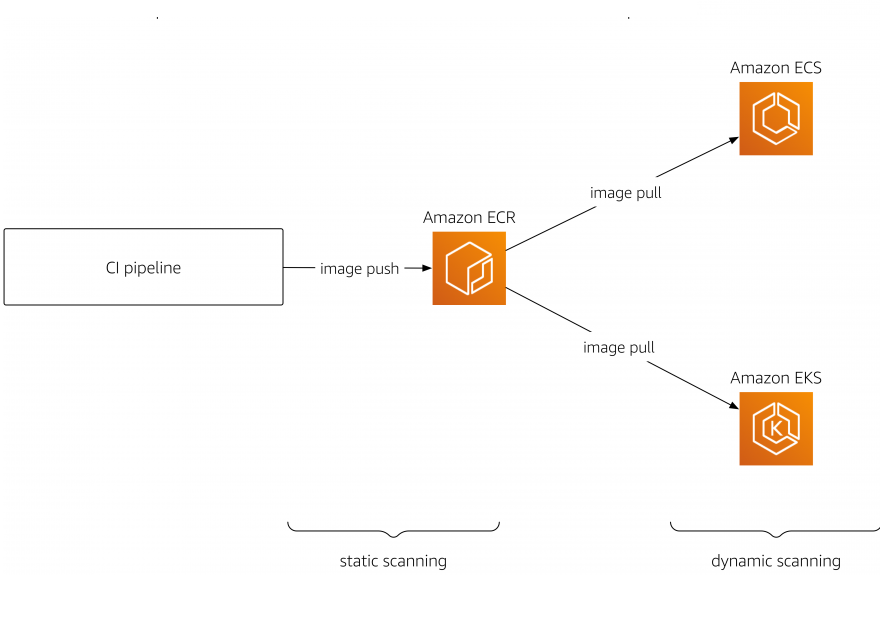
How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog

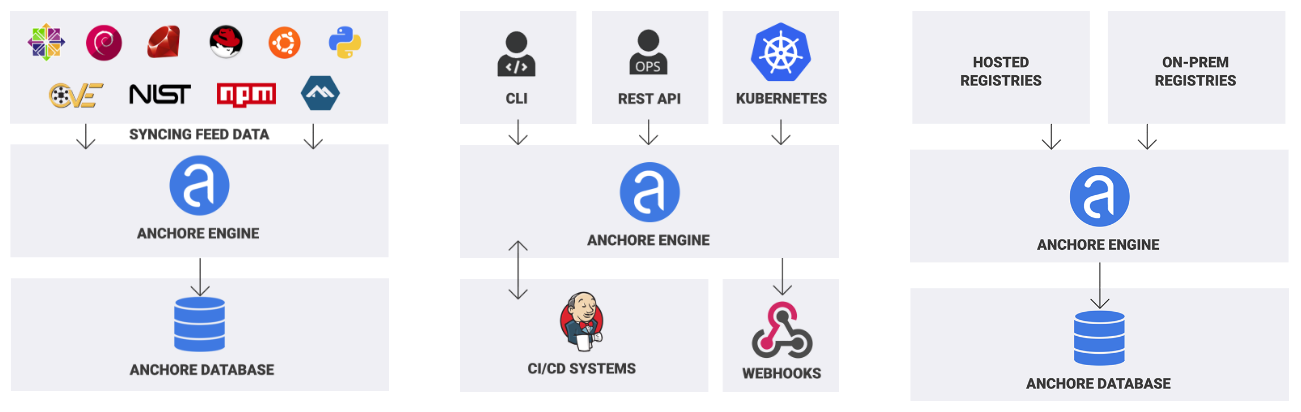
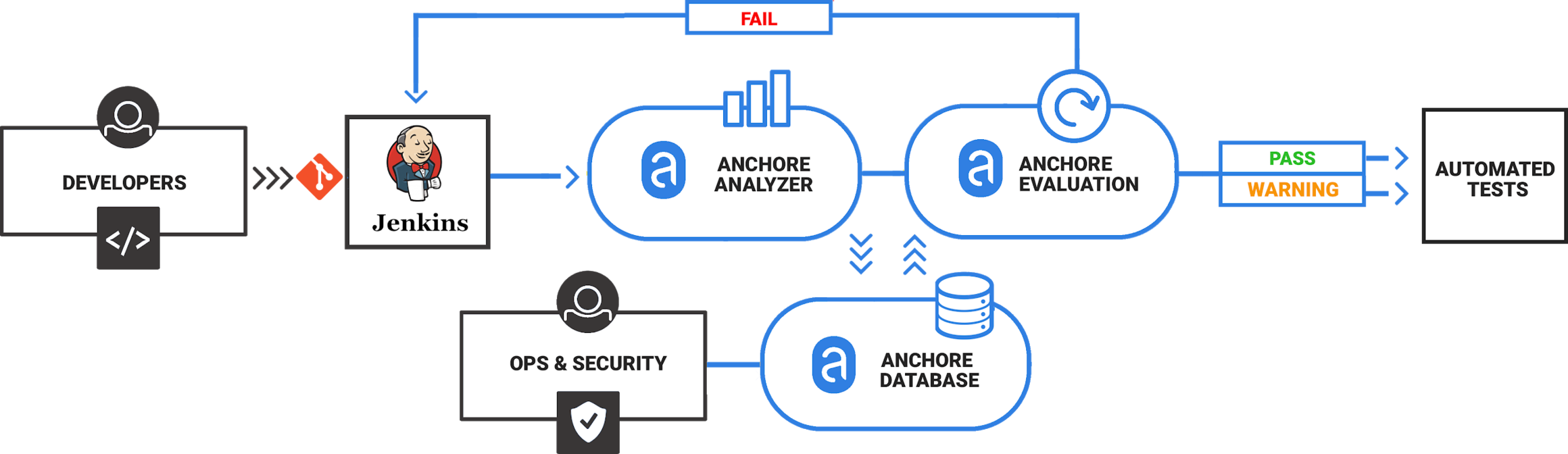
Docker Vulnerability Scanning Tools: Free, Open-Source, and Paid Options for Secure Container Images | by Hinanaseer | Medium